The Agile Release Train (ART) is among the focal concepts you must understand when learning about the Scaled Agile Framework (SAFe). So what is this terminology? And how important is it for business agility? Let’s find the answers to these questions in this article with Designveloper.
You should know this before knowing about the Agile Release Train: What is Agile Software development?
What is the Agile Release Train (ART)?
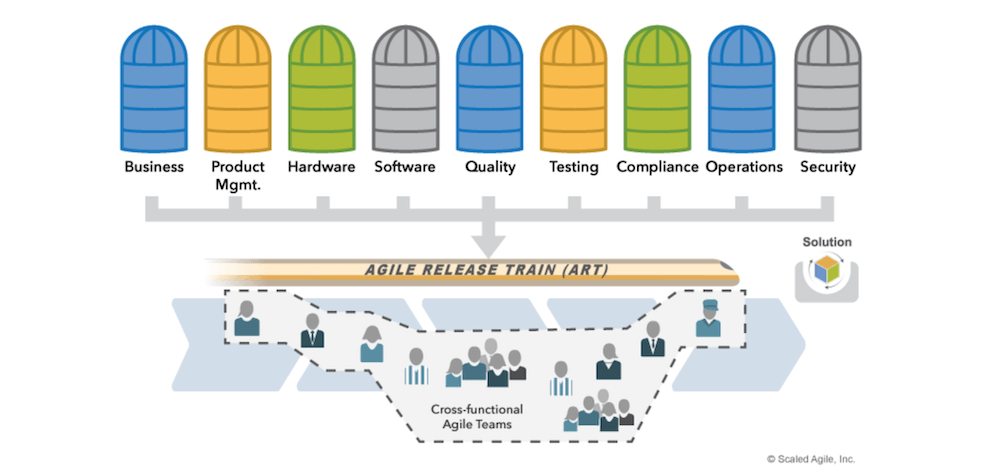
In SAFe, an ART is a self-managing, long-term team that consists of multiple agile teams. A typical ART includes 5 to 12 cross-functional teams, equivalent to 50 to 125 workers. Its main responsibility is to align those teams to a shared goal and mission. Further, agile teams wherein are navigated to regularly define, build, validate and release working solutions to end-users.
There are two other concepts relative to the ART you should learn about to better understand the train. They include Value Streams and Program Increments.
Agile Release Trains and Value Streams
Value Streams are a set of essential activities to turn business ideas into pragmatic solutions and then provide end-users with such deliverables. Which projects are conducted, Agile Release Trains need to be organized around such value streams. As multidisciplinary units, ARTs must have long-term experience and versatile capabilities to develop solutions that deliver perpetual value flow. Without operating around value, ART members struggle to monitor multiple dependencies and interconnections between teams.
There are four basic team topologies on a single ART, according to the SAFe:
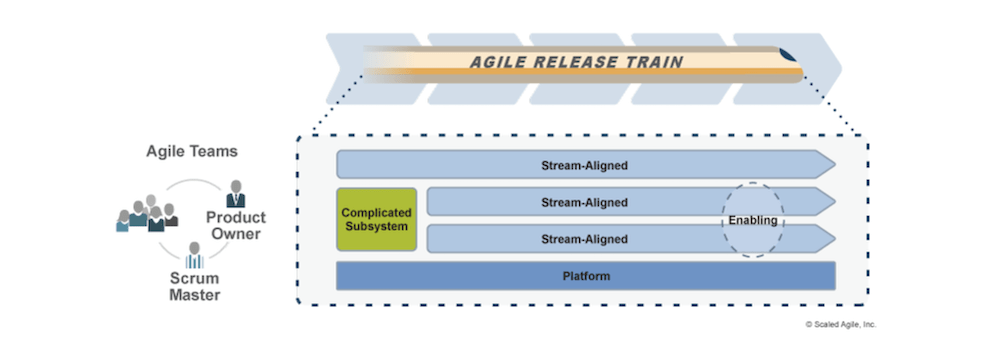
- A stream-aligned team operates around workflow and can deliver value directly to end-users.
- A platform team develops and supports platforms that offer other teams’ services.
- A complicated subsystem team operates around subsystems that require specific expertise and specialty skills.
- An enabling team helps other teams to use new technologies proficiently and improve specialized abilities.
Agile Release Trains and Program Increments (PI)
The concept of Program Increments (PIs) is mentioned throughout the ART’s principles, hence playing an important role in grasping ARTs. A Program Increment is a timeboxed phase through which an ART delivers incremental values of working solutions. A typical PI often includes four development iterations and one following phase known as Innovation and Planning.
In each PI, the ART will use synchronization and cadence to:
- plan the next increments;
- minimize work amounts in the process;
- collect values for feedback;
- ensure consistent retrospectives.
Who Gets Involved in Agile Release Trains?

The Agile Release Train fails to operate successfully without the presence of the following important roles:
- Agile Teams
Agile teams are the core feature of a single ART. Each team needs a team lead, a product owner and development members. They all must understand and apply the immutable values and tenets of the Agile Manifesto and SAFe to work towards common goals. ARTs can be launched in traditional agile, Scrum, Kanban or Extreme Programming (XP) environments.
- Release Train Engineer (RTE)
A release train engineer acts as a servant leader who supports implementing projects, removing obstacles, managing risks, and making continuous releases.
- Product Manager
A product manager is required to have a shared mission, vision, roadmap, and product backlog across an ART. Besides, the manager communicates with the product owner and customers to understand and discuss their demands.
- System Architect or Engineer
A system architect or engineer is held accountable for designing the high-level architecture of a system and identifying how parts fit well in the system. Also, the architect defines key system features, subsystems, non-functional requirements, and interfaces.
- Product Owners
On behalf of a business, product owners take responsibility for conveying business needs. They also need to ensure digital-enabled deliverables meet their requirements.
- End-Users
End-users are the ultimate customers of solutions.
Why are Agile Release Trains Necessary?
In a small-scale project, an agile team plays a vital role in planning, committing, and implementing the product development work. But when projects scale up or companies grow in size, a single team impossibly takes over increased workloads. It’s when the concept of the Agile Release Train (ART) is introduced to solve the problem.
All agile teams of the ART work based on three main criteria, including:
- Collaboration – More particularly, the train fosters the long-lived cooperation between cross-functional teams to plan, implement and deliver valuable products or services to end-users.
- Stability – The Release Train requires special skills and expertise to provide deliverables with business agility, flexibility, and sustainability.
- Autonomy – The ART is considered a virtual organization that is capable of operating independently to build business values.
For enterprises applying the Scaled Agile Framework, launching an ART is a must. The first train helps develop a suitable, reliable pattern for other upcoming trains and also builds a blueprint to duplicate its achievements.
Key Principles Behind ARTs

The Agile Release Train works on a wealth of essential principles, as described on the official website of Scaled Agile Framework:
1. Fixed Schedule
The ART plans and deploys tasks on a sound, fixed schedule that is identified by the Program Increment cadence. In case a feature misses a slot in the current PI, it will be built in the following one.
2. A New System Increment Every Other Week
The ARTworks in a two-week iteration, known as system increments. Accordingly, the train will deliver a new increment every two weeks. Further, team members use the System Demo to objectively assess the progress of the working system.
3. Synchronization
All agile teams of the ART will be synchronized into the common PI duration and have consistent start/end dates for each iteration.
4. Reliable Velocity
According to past data, the Agile Release Train can make sound estimates of how many new features can be built and deployed in a PI. Those estimations help members to make reasonable plans afterward.
5. Dedicated Workers
ART members are required to devote their full time to the train to maintain its sustainable performance and the solution’s ultimate quality.
6. In-Person PI Planning
The Agile Release Train periodically plans its work in an agile ceremony called PI Planning. This meeting is often organized around strategic priorities to prepare for the next PI. Although the face-to-face planning event is encouraged among members, its online counterpart proves effective at times.
7. Innovation and Planning (IP)
The Innovation and Planning session will be held at the end of each PI. This ceremony offers a buffer (an estimating guard band) and dedicated time for other activities such as PI planning, continuous learning, infrastructure work, or innovation.
8. Inspect and Adapt (I&A)
Like IP, the Inspect and Adapt event also take place at the end of a PI. During the session, the ART demonstrates and evaluates a deliverable’s current state. Moreover, a structured workshop is organized as well to determine backlog items that need improvements.
9. Development of Cadence and Release on Demands
The ART uses fixed cadence and synchronization to minimize the inherent variability that often arises during the development process. But the release is separated from the cadence. In other words, a deliverable or any of its features will be deployed and published whenever possible. This helps the ART deliver values to customers faster and receive prompt feedback for later improvements.
Conclusion
There’s no denying that the Agile Release Train is among the indispensable contributors to SAFe’s success. Through the article, Designveloper expects you to have a deeper understanding of how important ART is for scaling projects. This helps you draw out effective strategies to build and launch a high-performing ART.
The post What is Agile Release Train? Everything You Need to Know appeared first on Designveloper.
March 31, 2022 at 02:03PM